Five Ways to Change Your WordPress Password
With the dynamic nature of WordPress, creating, using, and maintaining strong passwords is critical. Passwords help keep the good guys in and the bad guys out, enabling you to run a safe, secure WordPress-powered website. In this DiW tutorial, we’re going to show you how to change your WordPress password in virtually any scenario: logged in, locked out, and everything in between.
Change password when logged in
The first and easiest way to change your password is to simply login to your WordPress Admin and update your User Profile page.
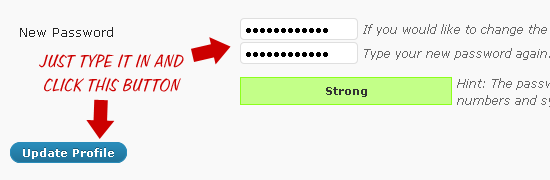 The easiest way to change the WordPress password
The easiest way to change the WordPress passwordThis works great, and is the intended way of changing your WordPress password if you are able to login to your account. But what if you aren’t able to login to change your password? If you forget your password, it is impossible to change it using the WordPress Admin. So..
Change password when locked out
The second way of changing your password takes this scenario into account. If you forget your WordPress password and are unable to login to change it, simply navigate to the “Forgot Password?” page and request a new one:
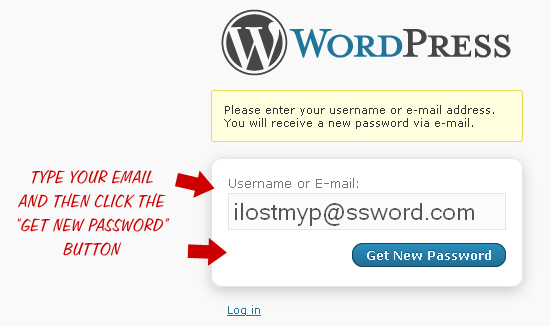 How to request a new password
How to request a new passwordThe password-reset page is generally located at:
http://domain.tld/wp-login.php?action=lostpassword..where domain.tld is the location of your WordPress installation. Once you request a new password, an email is sent to the email account with which you registered. In that email is a link to reset your password, which is finally sent back to your email account. The process takes a while, but seems to work fine assuming you have access to your registered email account. Without access to that email account, it is impossible to change your WordPress password using this method. So..
Change password like a ninja
The third way of changing your WordPress password bypasses the need for an email account by modifying the database directly. All that’s needed is a way of interfacing with your database. Here, we’ll be using the incredibly awesome phpMyAdmin.
To change the password directly via the database, simply login and locate the username of your account in the users table (click on the “Browse” tab to see a list of users). Click to edit the entry for your username, and then scroll to the user_pass field:
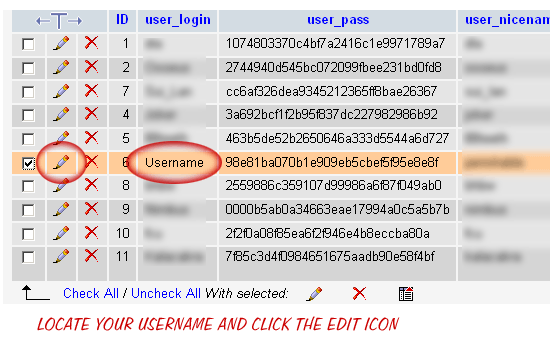 The WordPress users table with highlighted “user_pass” field
The WordPress users table with highlighted “user_pass” fieldAfter clicking the “Edit” button, you will see something similar to the following:
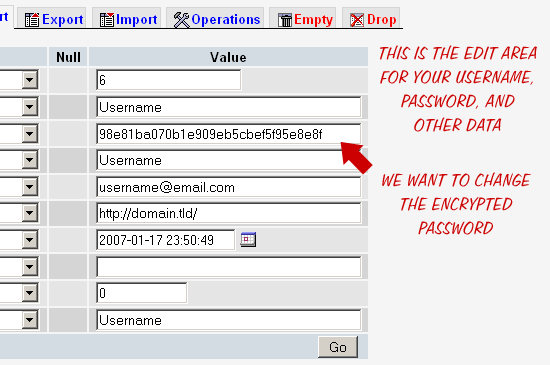 The Edit screen for your Username’s user data
The Edit screen for your Username’s user dataNotice the long string of random-looking text? That’s the MD5-encrypted version of your current password. You know, the one you forgot. To change it, you’re gonna need to encrypt your new password. To do this, you have several choices:
Encrypt a new password using a web service
The first way to generate a new MD5-encrypted password is to use a free web service such as this one. Simply enter your plain-text password (i.e., the complex phrase you want as your login password) and then click on the “Encrypt” button (make sure to select “MD5” as the encryption type). Once the service spits out the encrypted version of your password, copy and paste it into the user_pass field described above. Save your changes and you’re good to go.
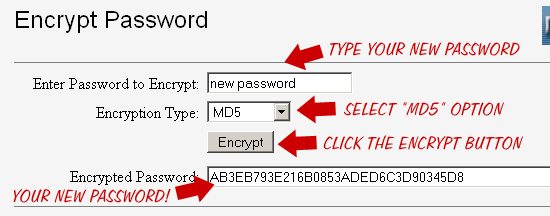 A free online password-encryption service
A free online password-encryption serviceEncrypt a new password automatically using phpMyAdmin
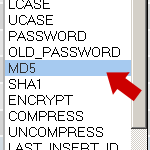
Of course, there is a much easier way of changing your password via the database. If you are using phpMyAdmin, simply enter the plain-text version of your new password in the user_pass field. Then, in the left-hand dropdown menu, select the MD5 option and click “Go”. This instructs phpMyAdmin to encrypt your new password with some fresh MD5 hash. That’s all there is to it.
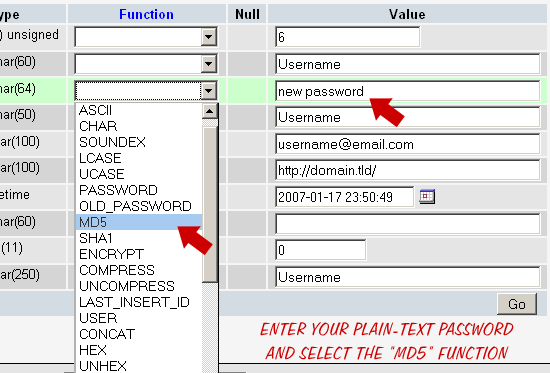 The MD5 encryption option next to the User_pass field
The MD5 encryption option next to the User_pass fieldEncrypt a new password via SQL query
The easiest way to reset your password with a MD5-encrypted hash is to simply execute the following query via the SQL command console:
UPDATE wp_users SET user_pass = MD5('newpassword') WHERE user_login = "admin";Before executing this query, change the newpassword string to your new password and edit the user-login name admin and table-prefix value wp_ if necessary.
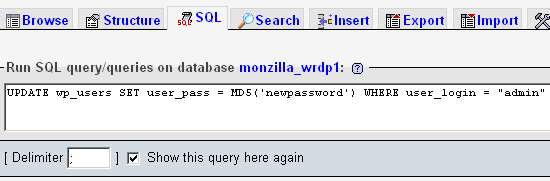 The SQL command console, locked and loaded
The SQL command console, locked and loadedViola! It’s that easy. Keep in mind that MD5 is designed for one-way encryption — you can use this method to encrypt new passwords, but you will not be able to decrypt existing passwords. It’s strictly a one-way street, so be sure to keep your passwords someplace safe to avoid having to do this again.
21 responses
-
nice article, I like how theres a database way incase you get locked out completely
-
wooow…what the third way is very….ninja ! ^^
-
WP passwords are salted. That putting straight MD5 into the database will not work.
Or it shouldn’t at least. If it does then WP is really insecure.
-
Great post as always!
Thanks for the database change of pass info. I have encountered the need to do this before and did not realize that I can encrypt via a web tool – though I should have.
Thanks.
-
“Change password like a ninja” jejeje, really funny title!!
i like the post, nice reading
thanks for share
-
Woah… totally didn’t know about the SQL one. Great post, and EXTREMELY clear. Great job!
-
Nice, Jeff, I hadn’t realised SQL had a MD5 datatype. Great tip, that’ll certainly save me some time.
-
Not sure what you mean by that, But MySQL doesnt have a MD5 datatype.. It does have a MD5 function however.
Last I saw, It was still suggested to MD5 data in the app before sending it accross the wire however, As MySQL logs can log MySQL queries, and a lot of MySQL servers on shared hosts are out of control of the user/etc. So its best to sent the hashed values instead.
-
Yep, I meant the function, tired brain. Its going to be useful for resetting passwords when clients really, really mess up a blog (yep, it happens).
-
I definitely agree sending unhashed data across a network is a bad idea, security wise. When I go to use this trick, I’ll generate a new password and set it from within WP afterwards.
-
-
-
Great post, Had a few of my blogs hacked last last month.
-
Enjoyed this post. Keeping this bookmarked for future reference
-
Good article.
I do find it odd that WordPress doesn’t salt the passwords for users. That’s basic security.
-
Nice, I love to look at one problem from multiple angles, very instructive. Thanks!
-
“like a ninja” hahaha btw I didn’t know that phpmyadmin knows how to md5
-
I like the last option better, cause i’ve been in the stage when i’ve lost my password… oopz ;)