Spam Link Injection Hacked (and How I Hopefully Fixed It)

Just recently my other blog CSS-Tricks was hacked. I first found out by a very helpful reader emailing me a screenshot from the mobile version of my site.
The mobile version of my site was built by Mobify, so I contacted them right away. As I should of known, of course Mobify can’t insert content into a site, they only are a presentation layer on top of the already existing content. They were very quick and helpful with their response and sent me some links to useful resources and infos.
Hacked.
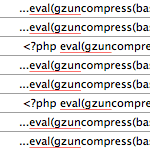
After seeing the following screen, I knew that the site itself was hacked. Time is of the essence at this point, because not only do I not want my visitors seeing nasty spam, I don’t want Google bot to cruise through and see the mess and hurt my SEO. I immediately set out to figure out where these spam links were being inserted from. Here’s what I was seeing on the site:
I had this happen to me years ago and it turned out the theme files themselves were altered and spam injected that way. I took a look through all of them quickly and didn’t see anything. I could see from the source on the site that the links were being inserted after the content on each post. I could also see at this point that the links were identical on each post. This seemed like a theme file injection to me, but clearly it wasn’t.
Database attack
I popped open the WordPress Admin itself and checked out a post. Low and behold, there the links were, right in the content for each post. I checked out a number of them, new and old, and there were all the same. At this point, there were two possibilities. The Admin was compromised giving someone access in there and the ability to edit posts or the Database itself was compromised.
Due to the speed of the attack, the fact that all the links were the same, and that over 500 Posts/Pages were identically altered, I concluded it must have been a database attack.
Here is what I did:
- I changed the Admin username and password. Just to make sure that the Admin itself was secure, this login and password must be changed. Since you cannot change usernames after they are created, I created a new account with a new password, logged in with that, and deleted the original account, attributing all posts to the new account.
- I changed the server admins username and password. My site is managed by Plesk, which has a login and password to itself. If someone had access to this, they could access the Database. It is unlikely this was compromised, but to cover all the bases, this was changed as well.
- The database name, database username, and database password was changed. Changing the database password might have been enough, but just to be as difficult as possible I changed both the username and the password. The database name was changed later after the cleanup (see below).
- I changed the FTP login and password. If the hacker had this, they could have altered the theme files or opened the wp-config.php file to find the database credentials.
- The XMLRPC file was removed. This file is used for pingback and trackbacks as well as remote editing possibilities like posting by email. I literally use none of these things, and this file has been responsible for security problems in the past, so I removed it.
- The file permissions where checked. In particular, I found the wp-config.php file was set at 775, I changed it to 755. I also made sure that none of the file were world writeable except the very few that need to be, like the uploads folder.
Spam injection
Here’s what the spam injection looked like:
<div style=\"\\64\\69\\73\\70\\6c\\61\\79:\\6e\\6f\\6e\\65\">
<a href=\"http://www.fcit.usf.edu/li/viagra.html\">viagra</a>\r\n<a href=\"http://www.fcit.usf.edu/li/free-viagra.html\">free viagra</a>\r\n
... lots more ...
</div>That “style” attribute (inline CSS), when rendered in a typical browser, converted to display: none; and thus were not visible. For whatever reason, when Mobify picked up this content, that weird string of characters wasn’t converted and thus the div was visible not hidden.
The reason I’m sure the hackers chose this technique is that the blog owner may never realize the links were inserted because they aren’t typically visible. I would think that Google doesn’t give any link credit to links that are in a container with display: none, but perhaps the hacker’s theory is that the google bot won’t be able to tell this div is hidden because of the weird code.
I would be interested to know if Google can be duped with this technique. It seems like they would be smart enough to detect it, yet I wouldn’t be surprised if the site is penalized anyway due to being compromised by spam.
How I Removed the Links
Luckily the code that was inserted in every single Post/Page was identical. I downloaded a fresh copy of the Database (as a .SQL file), opened it up in TextMate (any text editor with find/replace will do) and did a find/replace on the block of spammy code (replaced it with nothing). Then I saved a new copy of it and created a new database on the server (hence the change in DB name). I imported the new fixed SQL file and posted WordPress at the new database.
Crossing My Fingers
It’s been a week now, and no more problems. I pray that what I have done has fixed whatever the hole was, but of course I can’t be 100% certain because I’m not 100% certain what it was to begin with. Of course, posting all this information surely doesn’t make me any more secure but oh well. I of course have serious backups going on so the worst thing that can happen is I get hacked again and have to restore from backups and keep plugging holes.
Consequences
Although the spam wasn’t on my site for more than a few hours, someone has pointed out to me that my Google PageRank for the homepage has dropped from a reasonable and healthy PR 6 to ZERO. While PageRank is a very weird thing and it could be any number of things including a random inaccurate report from Google, it seems more likely this is a penalization from them for the spam. Many of my subpages, which get crawled far less frequently, still have their PageRank. It’s not just the PageRank, many searches that would have brought up the homepage (e.g. my own name) are now far down the SERP pages when they used to be #1. This of course will be seriously affecting my traffic until my PageRank is restored, if it ever is.
CSS-Tricks, is non-trivial portion of my income, and if there is a serious dip in traffic it could certainly affect me financially. I’m not whining, it just goes to show that site security is not some abstract nerdy hobby, it’s serious business that can have serious consequences.
26 responses
-
So glad you were able to recover and batten down the hatches! Thank you for sharing the details. Can’t Google help you recover your page rank if you contact them about what happened?
-
Yikes, man. That is scary. Do a followup a little later to let us know if that fixed everything.
-
You can request Google to reconsider your site. Login to you Google Webmaster Tools. Click on the account that you want reconsidered. Over on the left is “Help with” and below is “Reconsideration Requests.” There is a space to write an explanation. It will take them time. I hope you get it all straightened out with them. CSS-Tricks is a very helpful site.
-
This happened to several of my sites on March 4 I believe. On my Drupal sites, my template files were hacked. I also found it on some of my straight PHP sites. Due to the nature of it, I didn’t discover it right away until Google tagged my sites as spam sites. Once I was aware of the attack, it took awhile to find the affected file because the last update of the file hadn’t changed. I discovered it when I found a template file to be over 50k and normally it would be less than 10k. Cleaned up all the spam links, waited for Google to re-discover and I was good to go.
-
That sucks Chris. Glad you got it sorted so quickly.
I had a similar problem on a non wp site and lost all PR for the homepage. I never got the PR back to what it was. Not sure this will help but you could try contacting Google via their reconsideration page. Just tell them what happened and see what they say.
-
That’s crazy, stupid spammers. I guess that just shows, that you’ve got to make sure your ends are covered before your get massive hits and traffic.
-
what an experience…! End of the day im happy to see csstricks is doing okay !!:)
-
You know, I don’t hate many things in this world, but I do hate these freaking malicious hackers. I’ve dedicated a lot of my time to stopping them. My wife’s e-commerce site got hacked. The intruder uploaded a script which installed a “.gif” file in every folder labeled “image”. The file downloaded viruses to people’s computers.
I mean come on, really?
I love the good things you guys are doing over here. And I know what you mean by being worried about posting too much. I talk about blog security at times on my site and there’s always that little voice in my head telling me “you’re just inviting them to take a crack at it, John.”
Google took my wife’s site offline before I noticed the problem. I fixed it and then through Google’s Webmaster Tools (like others had mentioned) I informed them I fixed everything. The site came back online, but I lost 2 points in PR and traffic is way down.
One question. How did you figure out what the encoded code decoded to (i.e. the display:none)?
-
I’m glad to hear it’s all sorted out now. Finally, I have a reason I can tell people I built my own blog from scratch (past “I felt like it”)… even I can’t remember how the database works. Also, the admin area… doesn’t exist.
OK, perhaps I need to come up with a couple more reasons…
-
We have had this twice now over at 71squared.co.uk although our links were porn links and hidden unless you view the source, so not sure how long they were there for :(
-
Contact Google, whether through Matt Cutts or a more official method, and explain what happened to them. They have the power to fix it, and very well might help you out.
-
You said that you changed permissions of wp-config.php to 755. Rule of thumb,
files – 644
folders – 755 -
WPscan hasn’t been mentioned here yet and I think it deserves inclusion.
The security scan there is helpful, not to mention the entirety of the blogsecurity website. I’ve used it a couple of times on a few sites and it’s caught a few things that helped me lock things down. First thing I do these days w/wordpress – remove that admin account. I think that’s the root of a good number of vulnerabilities.
-
Scary. One thought springs to mind; I wonder how easy it would be to create a Yahoo pipe that took an RSS feed and made a feed of the raw source? At least if you were subscribed to that for your own sites you’d see the problem fairly quickly…
-
I’ve had a similar thing happen. I was just wondering, as of a month later, what the status is. Have you had further troubles with the spammer?
Thanks again for this guide and writing this post.
-
Exact same thing happened to me. Same links too. I think it was an exploit in the WordPress code so a malformed SQL query inserted all the links but I did all the things you did just to be safe.